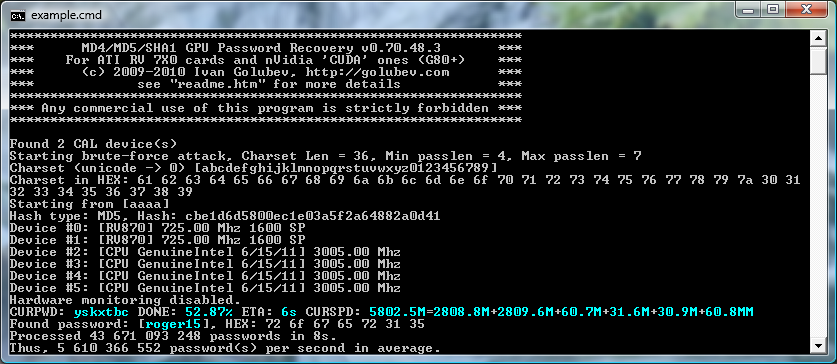
I have believed for a long while now that passwords need to go away. Further support for that position is provided by a PC Pro article called How a cheap graphics card could crack your password in under a second:
Now, I cannot imagine anyone managing to mandate a nine-character, mixed-case, random-character password on an organisation. But if you did, and you weren’t hanging from a tree by the end of the first working day, the CPU would take 43 years versus 48 days for the GPU.
He then went on to add in mixed symbols to create “F6&B is” (there is a space in there). CPU will take 75 days, GPU will take 7 hours.
What does this tell us? well, the stark reality is that even long and complex passwords are now toast. If you think you were being wise by forcing users to have randomisation in their passwords, then think again. It is utterly futile.
[…]
A GPU of the type used by this chap is not unusual or high end. It is standard-issue stuff. Indeed, I have just sat through the AMD presentation here at Computex in Taiwan, and they made a big deal about putting GPU power into netbooks offering 500Gflops, without denting its 12-hour battery life. And that’s shipping within months.
All I can say is this: you have been warned. It is time to think long and hard about password security, and how you do your authentication. This has crept up on us in the background, and we really haven’t been paying attention.
Some of us have been paying attention.

![[x]](/images/sigil_md.jpg) Blackmoor Vituperative
Blackmoor Vituperative